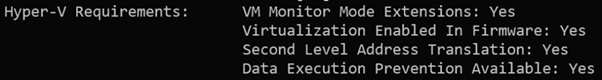
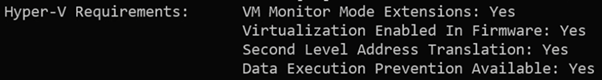
Dear Visitor,
I’m Alex Radzishevsky, welcome to my digital abode. I occasionally update this space whenever time allows.
I’ve been into the computing world for 35 years, I’ve seen and been a small part of its evolution. I held membership in Fidonet (2:461/113) and operated my own dial-up BBS back in the 90s. I’m still a fan of tracker music and the demoscene. And yes, I still use the old Norton-style file commander on my modern Windows computer.
You won’t find me on big social platforms such as Facebook et al. I like the more old-school ways of talking: email, chat, phone call, or meeting face-to-face. For me, these feel more real and hold more substance than the ephemeral interactions of modern-day ‘social’ networks. Plus, I have more fun things to do with my time.
If you want to get in touch, just send me an email. If you’re curious about my life, take a look around this site. I’ve shared what I’m okay with everyone knowing. And if you’re here for work reasons, my LinkedIn is the place to go. If you just want to see some pictures, check out my photo album. I add new ones when I can.
You’ll find my latest posts below.
Warm regards,
Alex Radzishevsky.
… >>> Click to read the full post...